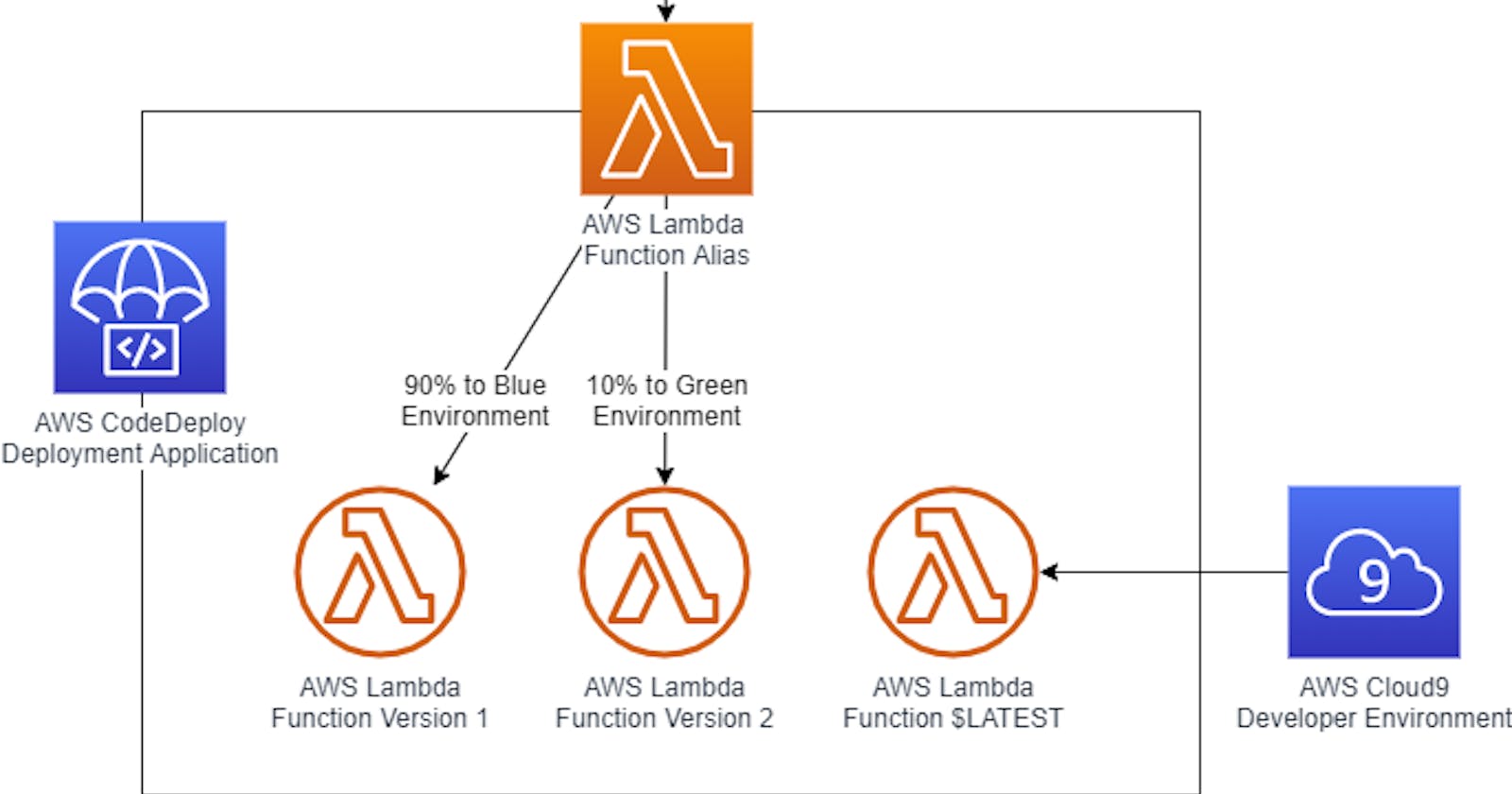
Serverless computing with AWS Lambda
Learn about how AWS lambda works in depth.
Introduction
Serverless computing is the most abstract method to use cloud's resources. We don't need to think about managing anything. You will need to focus on building and deploying apps, all other complex stuff is taken care by AWS.
AWS lambda
- AWS lambda allows to run your code without having to configure and mange servers. You will have to configure only CPU and memory.
- Scales automatically.
- Has built in code monitoring and logging using Amazon CloudWatch
- Uses IAM(Identity and access management) to provide a flexible permission model which defines who can run the functions.
- You only have to pay for the time when your code is running.
- Availability of triggers to specify which events can call the function which run the code.
Permissions
We have to deal with two kind of permissions in AWS lambda
- IAM Resource Policy
- IAM Execution Role
IAM Resource Policy
This policy deals with who can use this lambda function. We can specify the lambda function to act differently for different people or different roles. Different predefined policies can be used. The predefined policies are as follows.
- AWSLambda_FullAccess-> full access to develop and modify lambda functions
- AWSLambda_ReadOnlyAccess -> can only read lambda functions
- AWSLambdaRole -> Can invoke or call lambda functions
We can also configure our policies by using functional policies. The following is an example of read-only policy defined by the user. Refer to more policies here
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "permission",
"Effect": "Allow",
"Action": [
"lambda:GetAccountSettings",
"lambda:GetEventSourceMapping",
"lambda:GetFunction",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionCodeSigningConfig",
"lambda:GetFunctionConcurrency",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"lambda:ListTags",
"iam:ListRoles"
],
"Resource": "*"
},
}
- The sid(Statement id) is a sub id for your policies.
- The Effect determines whether the policy results is allow or deny.
- To put it together policy depicts that the user is allowed all the actions provided in the "Action" segment and the actions are applicable to all the resources.
- The resource policy also grants permission to lambda functions across AWS accounts.
Execution role
The execution role provides necessary permissions to interact with other services inside AWS. Consider you are having a database running at another container in AWS and your lambda function wants access to that. In situations like this, we can use execution role.
This role must be provided when creating a lambda function. We can also declare a trust policy with the role. A trust policy defines which trusted accounts can be assigned the role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
The principle defines who can the roles can be assigned to. The lambda.amazonaws com is a service principle and allow the AWS Security Token Service action. Refer to more policies here
The creator who is creating the lambda function and assigning the roles must have a iam:PassRole permission.
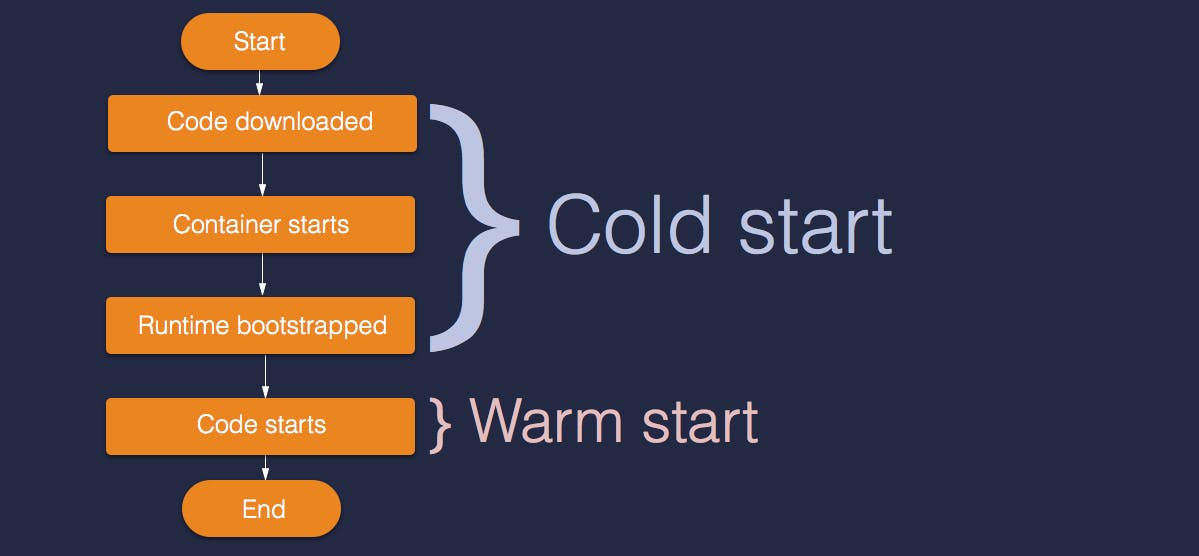
Lifecycle of lambda function
- When the function is called, the environment is to be prepared to execute the lambda functions. The execution environment is launched and bootstrapped for execution code. This is referred to cold start.
- If there are no triggers for functions, then lambda freezes the execution environment
- If a function is invoked when environment is in this state, it is referred to warm start. In warm start the, the frozen container is thawed and code execution occurs immediately without the process of bootstrapping.
- If a container becomes ideal for a long time, the execution environment is recycled and only cold start is possible.
Conclusion
- Amazon Web Services lambda is a very powerful feature and can be used to automate workload based on certain events.
- IAM Resource Policy and IAM Execution Role has to be configured to use lambda functions.
- The lifecycle of lambda functions has two type of starts called warm and cold start.